
COMP4108 — Fall 2012
Computer Systems Security
Due 11:59PM on MON OCT 15th
Due 11:59PM on TUES OCT 16th
Assignment out of 45 marks total
Please e-mail submissions (PDF) to:
dmccarney (àŧ) ccsl.carleton.ca Subject: COMP4108 A2
Framework code available here
Introduction
As mentioned on the General Page you will be completing this assignment from within a virtual environment provided to you. For each question include both your answer as well as the process by which you determined this answer. I.e. the exact commands you ran, and the output those commands provided. Also include any code you wrote, or scripts you edited.
~/.ssh/known_hosts. On Windows with Putty I believe you just have to accept the new key when prompted.
For this assignment you may work in pairs.
PLEASE BOTH SUBMIT YOUR GROUP'S CODE AS WELL AS A PDF REPORT.
You may use one, or both of the VMs assigned to you. Please have both members of your team submit the assignment, clearly indicating who your partner was.
Familiarize yourself with the
history command. You can use it to refresh your memory on commands you may have entered.You may prefer to use the
script command, which records input and output to a file automatically. See man script for more information.
At the end of Assignment 1 you saw how you could exploit a setuid binary with a race condition in order to gain root privilege on the box. Now what? If you were a real attacker it could be a matter of minutes before the system admin patches the vulnerable program and gives you the boot. How do you hide your traces? How do you install a backdoor that ensures you aren't a one-trick pony?
Linux Kernel Modules:
The answer to both questions (at least as far as this assignment is concerned) is a rootkit. A garden variety Linux rootkit is generally written as a Loadable Kernel Module or LKM. LKM's allow the system administrator to load new code to extend the kernel while the machine is running. Many device drivers are implemented as LKMs.
Only root can insert and remove modules (using insmod and rmmod respectfully), but it just so happens you're root today. Lucky you. There is a free guide to programming Linux Kernel Modules available online. This guide explains benign kernel module functionality, and you'll likely want to read (or at least skim) Sections 1, 2, 3, and 8.
This assignment assumes familiarity with the C programming language. If your C kung-fu is rusty you'll probably want to Google some reference material. The classic choice is the K&R book. The Carleton library has at least one copy. I also enjoy Learn C the Hard Way by Zed Shaw, available free online.
You'll want to make sure you understand pointers, memory management, arrays, and structures. You're a kernel programmer now.
Rootkits:
Rootkit LKM's alter the state of the system to present processes interacting with the Kernel sanitized information, or to add new functionality convenient for an attacker. A classic way this is done is by hooking system calls. For an idea of what system calls a processes invokes, you should revisit your use of the strace command in Assignment #1. The guide to programming Linux Kernel Modules introduces syscall hooking briefly.
To hide files from appearing in directory listings for instance, you would find the syscall that ls used to get filesystem directory entries and hook it. By hooking syscalls related to the filesystem a malicious rootkit might hide all files with a $sys$ prefix, allowing it to stash its own files from the system. Rootkits also frequently serve as backdoors that allow a user to elevate their priviledges, or get a remote shell without logging in.
Back to the Future:
You no doubt saw the grave warnings affixed to both the getdents man page and the LKM guide section on hooking syscalls. Not only are these warnings correct, things are worse than you might imagine. These techniques are dangerous, and often unreliable. No sane engineer would design their device driver in this fashion, we're hacking in the true definition.
The details in the LKM guide are unfortunately specific to Linux Kernel versions < 2.6.x and a 32bit architecture. We're living in 2012 and running Linux Kernel version 3.2.x on a 64bit architecture. This affects us in two major ways:
- The
sys_call_tablesymbol is no longer exported by the kernel to LKMs. This is to prevent developers from doing stupid things with it. We're going to have to find the address manually so that we can do stupid things with it. - The page of memory where the
sys_call_tablelives is now marked read only to prevent things from going wrong. We can't write a new hook into the table without first making the page writable, thereby allowing things to go wrong.
Writing a rootkit from scratch is going to be a grueling endeavour. Thankfully your connections in the underground have hooked you up with some super eleet warez. With their C code you should be able to write a respectable piece of kernel malware without losing your mind. Unfortunately your hookup only got you so far. The code's author must have uploaded it before it was completely finished. It looks like you'll have to pick up where they left off...
Important Notes:
You're writing code that runs in kernel space, with full privileges. The slightest mistake in your code is going to lead to legitimately weird things happening including (but not limited to):
All of the binaries on your system segfaulting. Including ssh.
Data being lost.
Kernel modules being stuck loaded.
Full kernel panics, leaving the box frozen
Don't keep anything on your VM you aren't ready to lose! Keep your code on your own machine and copy it over to compile/test.
You're going to want to work in very small, verifiable steps. Do not attempt to sit down and program the whole assignment. Instead, start with very small steps in mind and progress further only when you get that step working.
For example, in the file hiding task: start by figuring out what to hook, then try hooking it and keeping the original behavior in-tact. Once you can do that without crashing your VM, try printing all filenames in a directory to syslog from your hook. Once that's working start writing code to identifying files you want to hide from those being printed to syslog. Finally attempt to remove the entry from the results.
Reboot Request Tool
In order to deal with the realities of writing kernel code I've provided you a means to reboot your own VM. If your box becomes unresponsive, or any of the above listed things start happening you should use the reboot tool, examine /var/log/syslog and debug your rootkit code. Reboot your own VM as often as you require, remember to give it some time to boot up before you try to reconnect via SSH.
The reboot request tool will ask for your VM username/password and reboot the node that you are assigned. It will not ask for confirmation after you enter your username and password!
Part A - Setup (5 marks)
When in doubt, read the source code! The Linux Kernel is open source. I've placed the sourcecode for the version of the kernel your vm runs in:
/usr/src/linux-3.2.0. Another great online resource is the Linux Cross Reference.
- Download the rootkit framework code from the Introduction to your VM using
wgetor by copy pasting it into an editor. - Run
sudo bashto give yourself a bash shell with root privileges. We'll pretend that you got this from the race condition in A1. For most of this assignment you're going to be switching between a root user and a normal user, so I recommend you keep two windows open (the guru's might want to try my favourite terminal multiplexer, but it has a somewhat steep learning curve). - 1 Mark Find the address of the
sys_call_tablesymbol using the System.map - 0.5 MarksEdit the
insert.shscript to provide the right memory address for thetable_addrparameter in theinsmodcommand. It should be equal to the address you found in the System.map. - 0.5 MarksConfirm you can build the rootkit framework by running
make. You can safely ignore the warning about defined but not used variables, as you will be fixing that as you complete the assignment. - 0.5 MarksConfirm you can insert the rootkit module by running
./insert.shas root. - 0.5 MarksConfirm you can remove the rootkit module by running
./eject.shas root. - 2 Marks Fix the rootkit code so that the example
open()hook works. Show a snippet of the syslog output it generates once loaded.
There is a bit of logging in the incomplete framework. Run
tail /var/log/syslog to display the last few lines of the syslog. You may also want to try tail -f /var/log/syslog to interactively tail the syslog file. In interactive mode as new lines are printed to the log your terminal will update immediately. Press ctrl-c (that is ctrl and then c) to end the tail command and get back to the shell.
Part B - Backdoor (15 Marks)
-
5 Marks Write a new hook for the
execvesyscall using the framework code from Part A. Consult the execve man page to learn the details and function signature ofexecve(). You will need to know which__NR_Xdefine is used to find the offset insys_call_tableto hook forexecve(whereXwill vary syscall to syscall). You might find/usr/src/linux-3.2.0/include/asm-generic/unistd.huseful in this regard.
The hook should print the name of all files being executed, and the effective UID of the user executing the file to syslog usingprintk. Example output:
Oct 1 20:49:17 COMP4108-A2 kernel: [81423.749198] Executing /usr/bin/tail Oct 1 20:49:17 COMP4108-A2 kernel: [81423.749200] Effective UID 0 Oct 1 20:49:19 COMP4108-A2 kernel: [81425.950497] Executing /bin/ls Oct 1 20:49:19 COMP4108-A2 kernel: [81425.950499] Effective UID 1000
Thecurrent_*macros defined in the/usr/src/linux-3.2.0/include/linux/cred.hinclude will help you get the information you need to include in yourprintkmessage. -
10 Marks
Modify your hook code so that when the effective UID of the user executing an executable is equal to the value of the
root_uidparameter, they are given uid/euid 0 (i.e. root privs). Theroot_uidparameter must be via theinsmodcommand in insert.sh like the sys_call_table address, and not hard coded. Note that theroot_uidparameter should be set to the UID of the user you want to get root, not root itself. You will need to add this behavior.
Hint:In order to get full mark you must demonstrate the module working. Set the
The header file/usr/src/linux-3.2.0/include/linux/cred.hand the corresponding code in/usr/src/linux-3.2.0/kernel/cred.care likely of interest. Specifically, theprepare_kernel_cred(), andcommit_creds()functions.
root_uidparam ininsert.shequal to your user's UID, and provide the input/output from:
- Building the module code
- Runing
whoamias a normal user in one terminal - Inserting the module as a root user by running
./insert.shin a second terminal. - In your normal user terminal running
whoamiagain and being told you are root.
comp4108@NodeX:/A2/code/rootkit_framework$ whoami comp4108 comp4108@NodeX:/A2/code/rootkit_framework$ whoami root
Part C - File Cloaking (25 Marks)
ls and the OS provided directory abstraction.- 10 Marks Write a hook for the
getdentssystem call (man page here). Once again this will require finding the__NR_*define for the syscall number.
You will want to familiarize yourself with thestruct linux_dirent64definition available in/usr/src/linux-3.2.0/include/linux/dirent.h.
Your hook code should print the name of all directory entries returned by a call togetdents()to syslog usingprintk. Example output:
Oct 1 11:44:36 COMP4108-A2 kernel: [ 2266.441674] getdents() hook invoked. Oct 1 11:44:36 COMP4108-A2 kernel: [ 2266.441704] entry: rootkit.o Oct 1 11:44:36 COMP4108-A2 kernel: [ 2266.441706] entry: .rootkit.mod.o.cmd Oct 1 11:44:36 COMP4108-A2 kernel: [ 2266.441708] entry: .. Oct 1 11:44:36 COMP4108-A2 kernel: [ 2266.441710] entry: insert.sh Oct 1 11:44:36 COMP4108-A2 kernel: [ 2266.441711] entry: rootkit.c Oct 1 11:44:36 COMP4108-A2 kernel: [ 2266.441712] entry: rootkit.mod.c Oct 1 11:44:36 COMP4108-A2 kernel: [ 2266.441714] entry: rootkit.ko <snipped>
Hint:
Make sure your getdents() hook is coded with x86_64 architecture in mind. Most notably, you should be accepting a buffer with typestruct linux_dirent64 *not,struct linux_dirent*as the 2nd argument to your hook. -
15 Marks
Modify your hook such that the
struct linux_dirent64*buffer you return to the calling process does not include any dirent's for filenames that start withmagic_prefix. Themagic_prefixcharacter array should be provided as a kernel module parameter given toinsmodin theinsert.shscript. You will need to implement this parameter yourself.
After coding yourgetdentshook and implementing themagic_prefixparameter you'll want to test it in action:- Edit the
insert.shscript and set themagic_prefixparameter to$sys$ - Compile your module by running
make - Create a file called
$sys$_lol_hidden.txtin your current directory. - Perform a
ls -lto see if your$sys$_lol_hidden.txtfile was created. - Insert the kernel module by running the insert script
./insert.shas root. - Run the same
ls -lcommand to validate the$sys$_lol_hidden.txtfile is no longer included. It shouldn't be inls -laeither (i.e. isn't just a regular 'hidden' dotfile).
Hint:Example output (from normal user term):
If you use$sys$as yourmagic_prefixvalue you must remember to escape the$'s in the bash shell. The easiest way is to use\$instead of$when trying to create, edit, delete, or otherwise interact with one of your hidden files.
comp4108@COMP4108-A2:/A2/code/rootkit_framework/test$ touch \$sys\$_lol_hidden.txt comp4108@COMP4108-A2:/A2/code/rootkit_framework/test$ ls -la total 8 -rw-rw-r-- 1 comp4108 comp4108 0 Oct 1 11:59 bar.txt -rw-rw-r-- 1 comp4108 comp4108 0 Oct 1 11:59 baz.txt -rw-rw-r-- 1 comp4108 comp4108 0 Oct 1 11:59 foo.txt -rw-rw-r-- 1 comp4108 comp4108 0 Oct 1 12:00 $sys$_lol_hidden.txt comp4108@COMP4108-A2:/A2/code/rootkit_framework/test$ ls -la total 8 drwxrwxr-x 2 comp4108 comp4108 4096 Oct 1 12:00 . drwxrwxr-x 5 comp4108 comp4108 4096 Oct 1 11:59 .. -rw-rw-r-- 1 comp4108 comp4108 0 Oct 1 11:59 bar.txt -rw-rw-r-- 1 comp4108 comp4108 0 Oct 1 11:59 baz.txt -rw-rw-r-- 1 comp4108 comp4108 0 Oct 1 11:59 foo.txt
Hint:
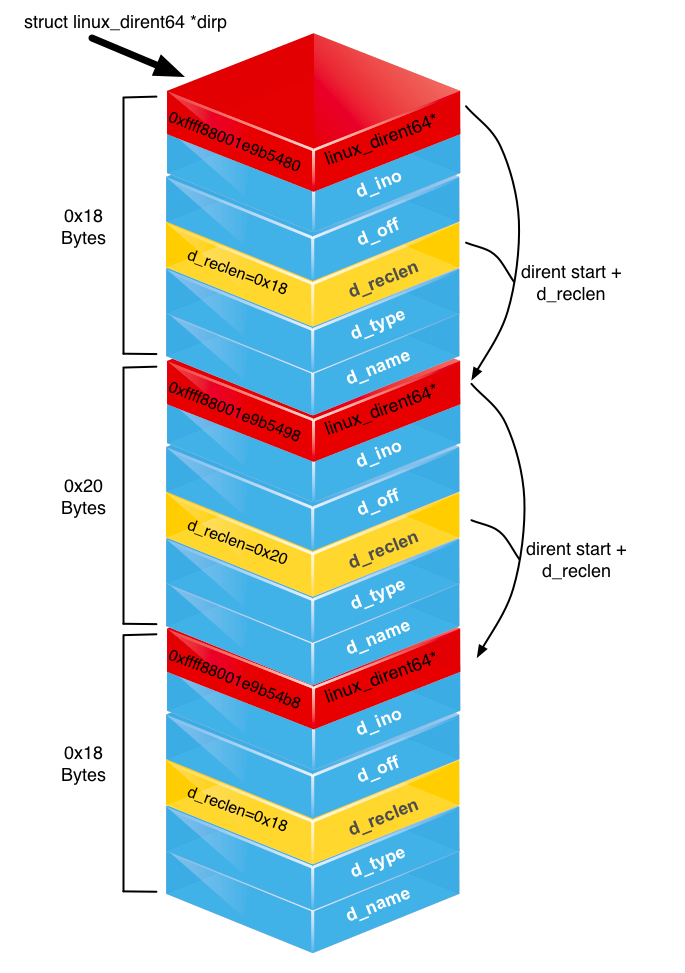 Modifying the buffer of
Modifying the buffer of dirent64's to hide files is the trickiest bit of the assignment. Luckily it is no more difficult than a typical data structure question (with a few twists).
Your objective is to sanitize thestruct linux_dirent64 *dirpbuffer provided as the 2nd argument to thegetdentssyscall. This buffer is allocated by the calling process (i.e they make sure there is enough memorymalloc'd for thestruct linux_dirent64s that the syscall puts into the buffer.)
The most important thing to know is that thedirpbuffer is not an array ofstruct linux_dirent64's of equal size. To save memory eachdirent64struct is only as big as it needs to be. In order to allow iterating through thedirent64structs in the buffer eachdirent64struct stores its length to be used as an offset to the nextdirent64in the buffer (see the figure). You will need to use this knowledge to determine how you can remove adirent64from the buffer. The man page forgetdents()has example code for iterating the buffer.
The second most important thing to know is that thedirpbuffer is userland memory You can not edit it directly or bad things will happen. Instead you must first allocate a kernel memory buffer of equivalent size. To do this you must usekallocandkfreenot their user-land counterpartsmallocandfree. Once you have a kernel buffer of the right size you can use thecopy_from_userandcopy_to_userfunctions to copy the userland buffer into your kernel buffer and vice versa.
So, the steps are:
- Call the original
getdents()syscall with thedirpbuffer your hook receives to have it populated withdirent64structs. - Allocate a kernel buffer of the correct size using
kmalloc - Copy the userland buffer into your kernel buffer using
copy_from_user - Perform your edits on the kernel buffer to remove any
dirent64structs you don't want seen. - Copy your edited kernel buffer into the userland buffer with
copy_to_user - Call
kfree()on the kernel buffer to free it and avoid a leak.
- Edit the
